Trojan horse backdoor virus 2025
Trojan horse backdoor virus 2025, What are Trojan Viruses and How Do These Threats Work Top Cloud 2025
$70.00
SAVE 50% OFF
$35.00
$0 today, followed by 3 monthly payments of $11.67, interest free. Read More
Trojan horse backdoor virus 2025
What are Trojan Viruses and How Do These Threats Work Top Cloud
What is a Trojan How this tricky malware works CSO Online
Trojan Vs Virus Vs Worm What Is The Difference
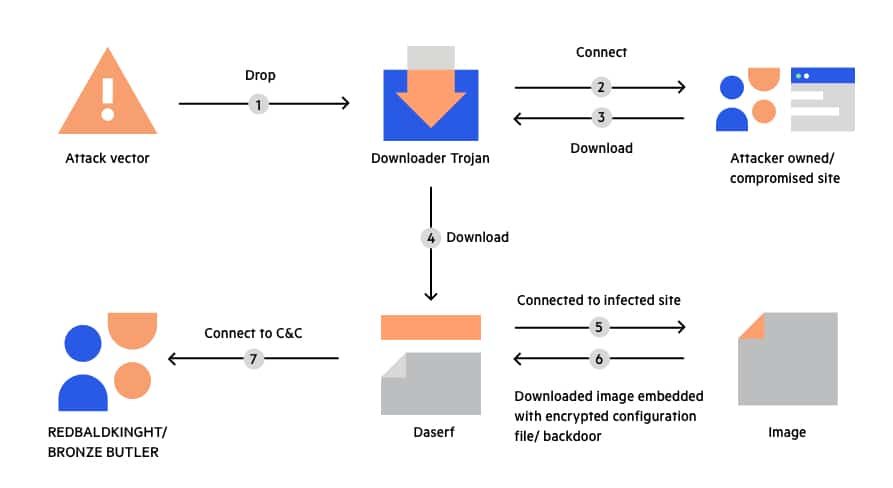
New Trojan Backdoor Malware Targets Mac OS X And Linux Steals
What is a Trojan Virus Trojan Horse Malware Imperva
Trojan Horse Meaning Examples Prevention
Description
Product code: Trojan horse backdoor virus 2025
What is a Trojan Virus Trojan Horse Malware Imperva 2025, Trojan Horse Meaning Examples Prevention 2025, What is a Trojan horse virus Types of Cyber Threats ESET 2025, What is a Trojan Horse Virus Types Prevention in 2024 2025, Trojan virus backdoors PPT 2025, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses 2025, What is a Trojan Horse Virus Types and How to Remove it 2025, What Is a Backdoor Attack Pro Tips for Detection Protection 2025, What Is a Backdoor Attack Pro Tips for Detection Protection 2025, Trojans and backdoors PPT 2025, What is a Backdoor Attack Shell Trojan Removal Imperva 2025, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet 2025, Computer under attack trojan virus worm and backdoor Stock 2025, What is a Trojan Horse Virus Types and How to Remove it 2025, What is a Trojan Horse Virus Definition Examples Removal Options Video 2025, Trojan Virus Unmasked What You Need to Know Silent Quadrant 2025, Trojan Horse Meaning Examples Prevention 2025, Trojans Backdoors Rootkits Viruses and Worms ppt video online 2025, What is Backdoor Attack Examples and Prevention 2025, What are Trojan Viruses and How Do These Threats Work Top Cloud 2025, Trojan Horse Virus Examples How to Defend Yourself 2025, Trojan horse removal Protecting Troy 2025, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus 2025, What is a Backdoor Attack Tips for Detection and Prevention 2025, trojans Backdoors Viruses and Worms Pianalytix Build Real 2025, Worms Trojans Backdoors ppt download 2025, Backdoor Trojan Black Glyph Icon Royalty Free Vector Image 52 OFF 2025, Trojan horse virus hi res stock photography and images Alamy 2025, Trojans and backdoors PPT 2025, Trojan Horse Demonstration with Metasploit Framework Payload 2025, Backdoors an overview ScienceDirect Topics 2025, What are Trojan Viruses and How Do These Threats Work Top Cloud 2025, What is a Trojan How this tricky malware works CSO Online 2025, Trojan Vs Virus Vs Worm What Is The Difference 2025, New Trojan Backdoor Malware Targets Mac OS X And Linux Steals 2025.
What is a Trojan Virus Trojan Horse Malware Imperva 2025, Trojan Horse Meaning Examples Prevention 2025, What is a Trojan horse virus Types of Cyber Threats ESET 2025, What is a Trojan Horse Virus Types Prevention in 2024 2025, Trojan virus backdoors PPT 2025, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses 2025, What is a Trojan Horse Virus Types and How to Remove it 2025, What Is a Backdoor Attack Pro Tips for Detection Protection 2025, What Is a Backdoor Attack Pro Tips for Detection Protection 2025, Trojans and backdoors PPT 2025, What is a Backdoor Attack Shell Trojan Removal Imperva 2025, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet 2025, Computer under attack trojan virus worm and backdoor Stock 2025, What is a Trojan Horse Virus Types and How to Remove it 2025, What is a Trojan Horse Virus Definition Examples Removal Options Video 2025, Trojan Virus Unmasked What You Need to Know Silent Quadrant 2025, Trojan Horse Meaning Examples Prevention 2025, Trojans Backdoors Rootkits Viruses and Worms ppt video online 2025, What is Backdoor Attack Examples and Prevention 2025, What are Trojan Viruses and How Do These Threats Work Top Cloud 2025, Trojan Horse Virus Examples How to Defend Yourself 2025, Trojan horse removal Protecting Troy 2025, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus 2025, What is a Backdoor Attack Tips for Detection and Prevention 2025, trojans Backdoors Viruses and Worms Pianalytix Build Real 2025, Worms Trojans Backdoors ppt download 2025, Backdoor Trojan Black Glyph Icon Royalty Free Vector Image 52 OFF 2025, Trojan horse virus hi res stock photography and images Alamy 2025, Trojans and backdoors PPT 2025, Trojan Horse Demonstration with Metasploit Framework Payload 2025, Backdoors an overview ScienceDirect Topics 2025, What are Trojan Viruses and How Do These Threats Work Top Cloud 2025, What is a Trojan How this tricky malware works CSO Online 2025, Trojan Vs Virus Vs Worm What Is The Difference 2025, New Trojan Backdoor Malware Targets Mac OS X And Linux Steals 2025.